Microsoft 365 - ATP Safe Links
This support article has been created for AntiPhish customers who use Safe Links and want to whitelist our phishing link domains.
By Domain
Navigate to Policies & rules > Threat policies > Create safe links policy
- Name your policy something easily identifiable, such as "AntiPhish - ATP Bypass Policy".
Description: This policy stops ATP rewriting URL links within phishing simulation emails. - Add users, groups and domains that will have the policy assigned to them.
- Under Protection settings, ensure the following settings are used:
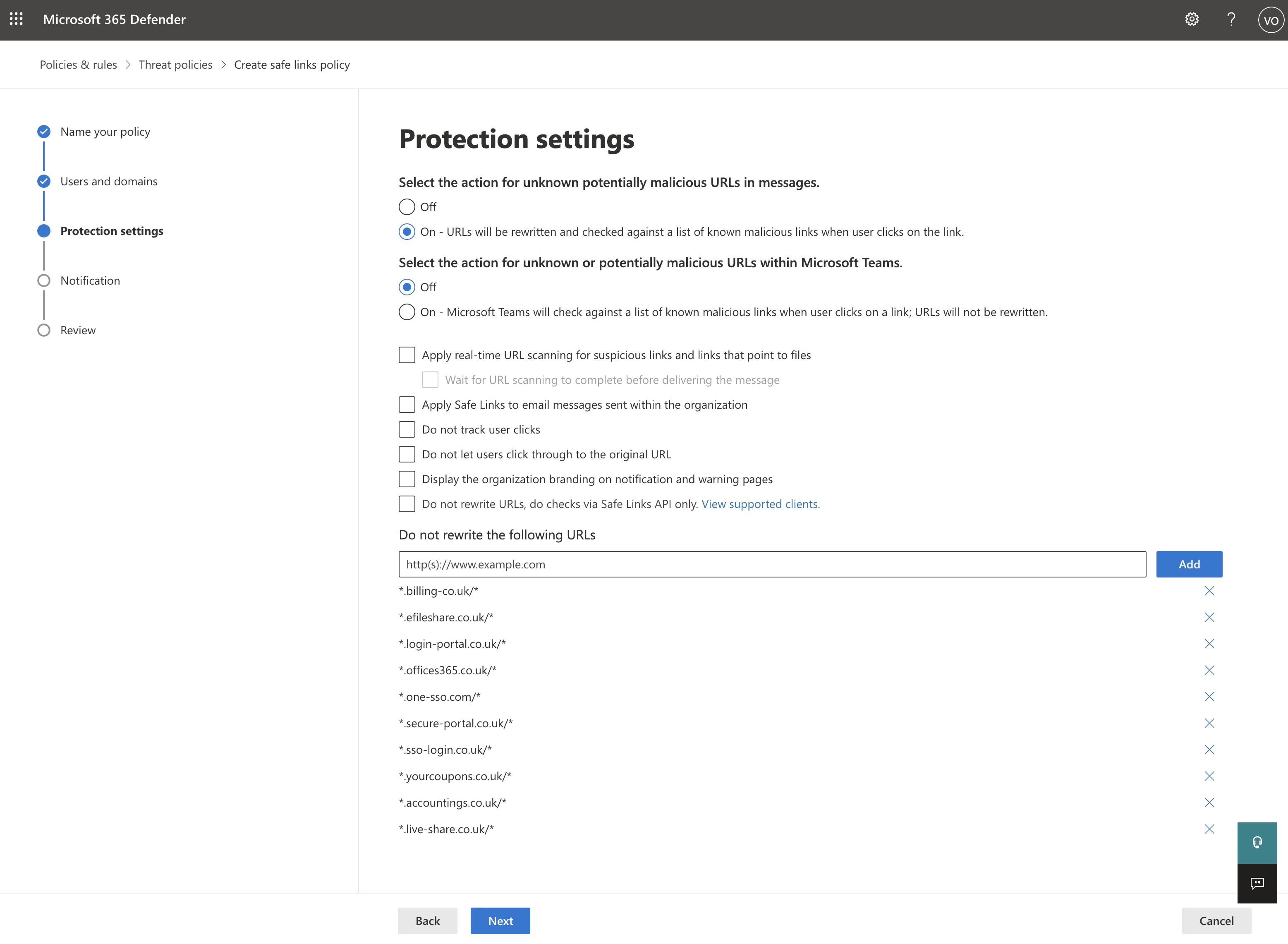
Do not rewrite the following URLs:
*referrals.ltd/*
*no-replies.co/*
*msoft-app.co.uk/*
*promotions-co.uk/*
*sharedfiles.co.uk/*
*wwwbilling.co.uk/*
*acc-system.co.uk/*
*sharefile-co.uk/*
*sso-signin.co.uk/*
*apistech.co.uk/*
Note: Domains are prefixed with * to include any potential subdomains used in phishing simulations, and suffixed with /* to include unique parameters required to gather user metrics. - Under Notifications, select how you would like to notify your users.
- Review your policy rules, then click Submit
By IP
You will need to add a Microsoft Advanced Threat Protection (ATP) rewrite rule to allow outbound traffic to our phishing server and prevent ATP from rewriting links, this also reduces false positives and helps users reach training. You can do this by IP here:
- In your Exchange or Office365 admin control panel create a new mail rule.
- Name the mail rule ‘AntiPhish ATP Bypass IP’.
- Click on more options and ‘Apply this rule if’ the select ‘The Senders’ and then ‘IP address is in any of these ranges or exactly matches’.
- Enter the IP address of the phishing server - 142.93.32.36
- From the ‘Do the following’ drop down menu choose ‘Modify the message properties’ and then ‘Set a message header’.
- Click the first ‘*Enter text…’ element and input ‘X-MS-Exchange-Organization-SkipSafeLinksProcessing’ and in the second ‘*Enter text…’ simply add ‘1’.
By Header
You will need to add a Microsoft Advanced Threat Protection (ATP) rewrite rule to allow outbound traffic to our phishing server and prevent ATP from rewriting links, this also reduces false positives and helps users reach training. You can do this by header here:
- In your Exchange or Office365 admin control panel create a new mail rule.
- Name the mail rule ‘AntiPhish ATP Bypass Header’.
- Click on more options and ‘Apply this rule if’ the select ‘A message header...’ and then ‘includes any of these words’.
- Go to More options... and then
- Click More options.... and then *Enter text... and *Enter words...
- Specify the header name - X-APHISH or input your own assigned header provided to you.
- Click *Enter words... then type AntiPhish, then click the plus sign.
- From the next dropdown menu, select Do the following… then set a message header.
- On the first *Enter text... and set the message header to 'X-MS-Exchange-Organization-SkipSafeLinksProcessing' without the single quotes.
- On the second *Enter text... just put the value to '1'.
Validating
After this stage has been completed, ask your assigned consultant for a test to be sent using our chat service found here.
Domains Last Updated - 13/11/2023
Please note, the image above may not reflect the current domains used for AntiPhish.
Want to talk to a human?
Feel free to contact us if you cannot find what you are looking for in our help center. We will be answering you shortly!
Feel free to contact us if you cannot find what you are looking for in our help center. We will be answering you shortly!
Contact us